Abstract
The prime objective of this project is to deploy a wireless LAN (Local Area Network) in a SOHO ambiance. As a network consultant, the goal is to administer an appropriate resolution for an IT company named Utopia Tech. Utopia is a SO(Small Office), established to provide gratifying assistance to clients utilizing advanced & innovative technology in every possible way. This report about WLAN infrastructure design incorporates details about the site survey, utilization of site survey tools, designs, justifications, and consideration of hardware, software, and other ample information. Likewise, the project further comprises security requirements during the WLAN deployment along with crucial features like reliability, scalability, and easily maintainable for future use. Scant obstacles during the process are carefully taken care of and appropriate actions are taken to avoid them from the deployment process.
1. Introduction
Internet, also known as ‘Net’ is a globally connected wide area network system that permits users to communicate and access the required data from anywhere around the globe. The Internet, being so powerful, draws people within it for some kind of interaction. From logging on to a social newsfeed to being updated or with expectations of sociability, the internet is an indispensable part of one’s life (Porter, 1997). All these connections are provided in multiple forms which also includes Wireless Network. Wireless network is further broadly divided into four major types: Wireless PAN, Wireless LAN, Wireless MAN, and Wireless WAN.
1.1 Background
WLAN, also known as Wireless Local Area Network is a wireless communication that uses high-frequency infrared radio waves, to establish connections between devices or to convey data from one point to another, without wired cables. The foremost aim is to deploy a wireless LAN on the premises of Utopia Tech. This is to ensure that staff and visitants can access strong internet communication along with the required software. So, the site survey is conducted By applying requisite tools, and the selection of hardware and software is recommended with applicable justification.
1.2 Assumptions
During the analysis and deployment study process, the following assumptions were put together for
Utopia Tech :
- The area of Utopia Tech is estimated to be around 1800 square feet
- The office is located at the distance of 45km from Pokhara Metropolitan City
- There are total of four rooms which includes lobby and reception area
- Currently, 12 employees work in Utopia Tech. Everyone working in the office as well as guests are to be provided with the network access
1.3 Project Scopes & Limitations
Project Scopes
- Implementation of WLAN Network with conduction of site survey and selection of appropriate hardware and softwares
- To establish easy way of communication in between departments and with co-offices
- Customers and staffs can be facilitated with mobile and swift internet connection for their work
Project Limitations
- Occasionally, environmental intrusions also fabricate barriers in network connection
- Undesignated Budget for the project create doubts while choosing the appropriate hardwares and softwares
2. WLAN Site Survey
To acquire the required information, a physical survey of the site territory is conducted. This is called a site survey. A standard wireless device with testing tools is used to examine coverage, propagation and factual performance of WLAN network(ZVANOVEC et al.,2003). Moreover, site survey conduction helps spot interference which further intercepts, The confinement of radio frequency. A formal interview is conducted to gather data and suitable placement of cables, access points, and other appliances is studied. As per the recommendation of Cisco, relevant knowledge of IEEE 802.11 Wireless and Wireless LAN Design is advantageous in conducting an effective site survey.
2.1 Site Survey (Types and Process)
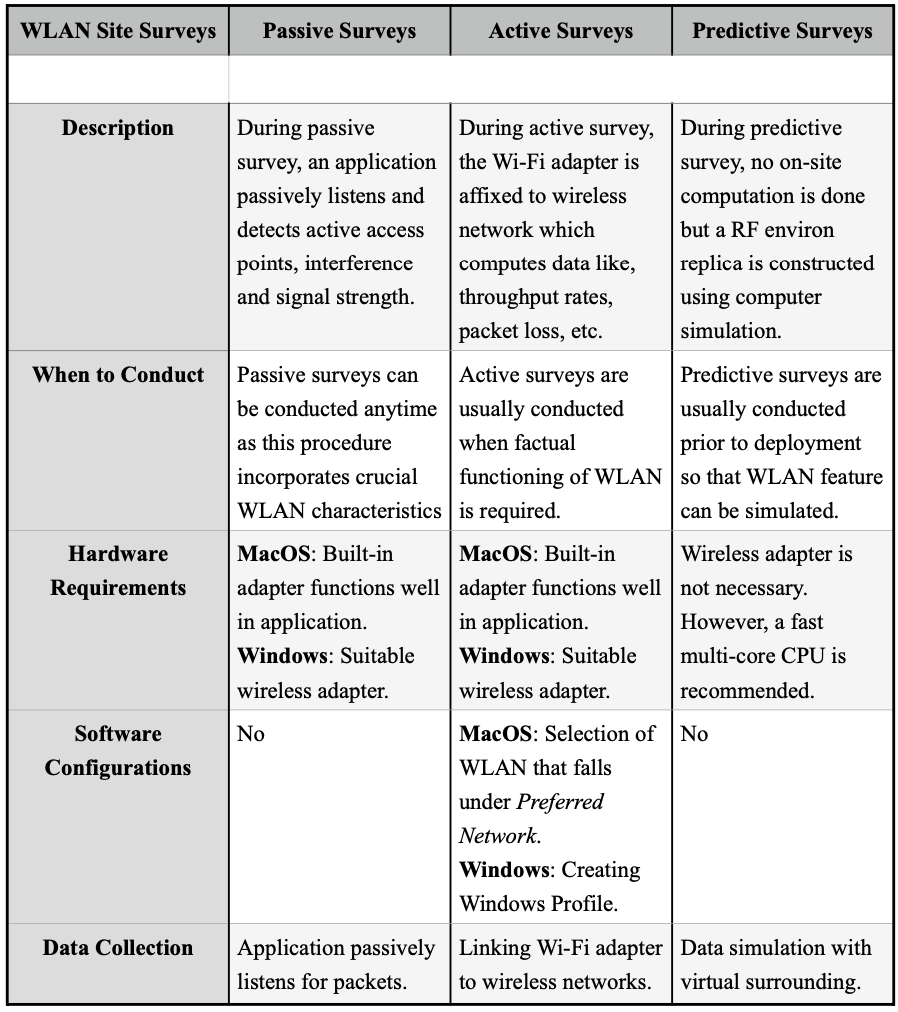
There are three major types of wireless site surveys: passive surveys, active surveys and predictive surveys.
1. Passive Survey: This is the type of site survey that is performed in listening mode. The application passively pays attention to WLAN traffic and discovers the level of noise, signal stability, and functional access points.
2. Active Survey: This is the type of site survey where wireless adapters are linked with access points, to take measurements of throughput rates, retransmissions, packet loss and other crucial details.
3. Predictive Survey: This is the type of site survey where the RF environment is created without any on-site computation.
Comparison between Site Survey methods
2.2 Requirement Elicitation
Requirement elicitation is an investigative process of accumulating essential data with continual interactions with relevant stakeholders. The process includes genuine exploration and documentation of information that clarifies what the project demands for its realization. With effectual interaction with end users and stakeholders, requirements are gathered about what and how the project should come into execution. Moreover, requirement elicitation also results in evident functional requirements of the project. Depending upon the condition and type of projects, several methods can be used to collect information from relevant users, clients, and stakeholders. Requirement gathering are performed in the following ways:
2.2.1 Business Requirements
Stakeholders Requirements
- The deployment planning should be economically and practically feasible
- There should be no complaints about network connectivity from employees or clients
- The deployed hardwares / softwares should be scalable
Functional & Non-functional Requirements
- The WLAN system should be efficient and support high number of nodes
- The deployed system should cover all office with strong internet connection
- The deployed WLAN must be highly secured from any possible threats
- WLAN policies should be enforced to make connection safe for users
2.2.2 Interviewing Stakeholders
In order to acquire more guidance, direction and assemble additional requirements, an interview including questionnaire is conducted with employees and clients. The figure below displays few questionnaires which are asked while interview process.

2.2.3 Determining Physical & Data Security Requirements
When the usage of network increases, security requirements are to be upgraded as well. Both, physical as well as data security are crucial in order to use the network with reliability and without inconveniences.
Issues within Radio Frequency, such as freezing and detachment of connection between devices must be carefully studied. Shielding constituents with metal or glass wares can solve physical security complications. Likewise, for data security, transmission of data must be sealed and unambiguous, which can be done with different virtual network technologies.
2.3 Site Survey Types (Analysis and Recommendation)
After all the obtainable requirements are gathered, a feasibility study is conducted in order to analyze the most effective and appropriate method of site survey.
Regarding technical feasibility, active site surveys are found to be the most advanced. Precise measurement of signal propagation and radio frequency makes this process effectual, as it covers contents like walls, furniture, ducts, and other influential elements. Similarly, in terms of operational feasibility, an active site survey is pretty efficient as it computes real throughput rates and performance of every access point placement. In contrast, the economical feasibility determines the passive survey to be the most economical one as it requires little manpower and is easy to conduct among all three types. Predictive surveys can be commanding when there are complications in accessing the site location(Sauter, 2018).
Out of all three types of site surveys (Passive Survey, Active Survey, and Predictive Survey), the chosen type is Active Site Survey. This is because an active survey provides precise statistics about performance for every access point and guarantees the installation process. Moreover, despite being labor intensive, active site survey requires very few number attempts to conduct the site survey process.
2.4 Current Site Design and Details
As a network consultant, a well planned process is required in order to implement the WLAN Network effectually. For this, a comprehensive study is done by constructing an appropriate design, where all the requisite factors are considered.
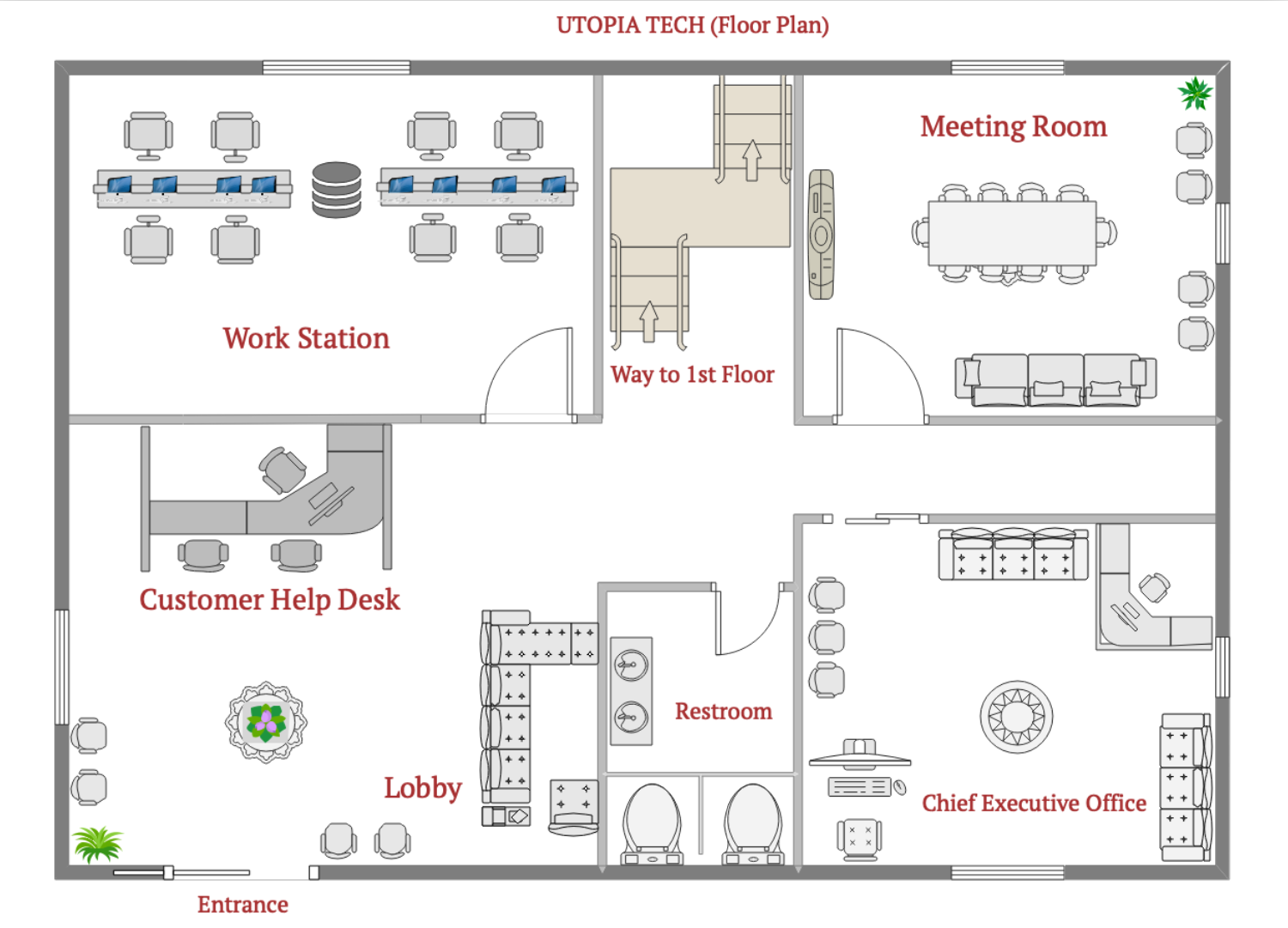
2.4.1 Physical Location & Characteristics
Floor Plan of Utopia Tech
While studying the floor plan of Utopia SOHO circumstances, several barriers that affect which affects wireless signals are discovered. Generally, physical obstacles are supposed to cause excessive interferences, having an impact on network coverage, standards, and eventually on performances. Frequency is measured using frequency bands of certain ranges and essential rectifications are done.
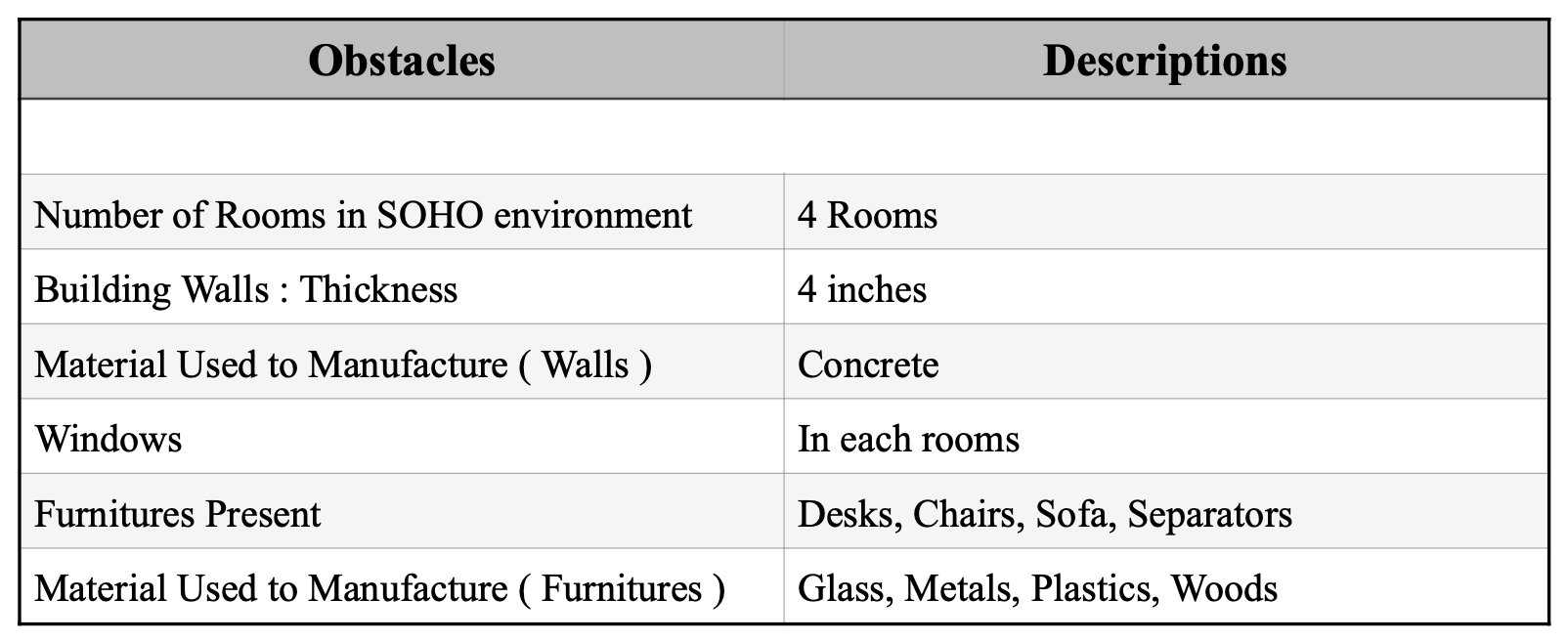
2.4.2 Obstacles within the Site
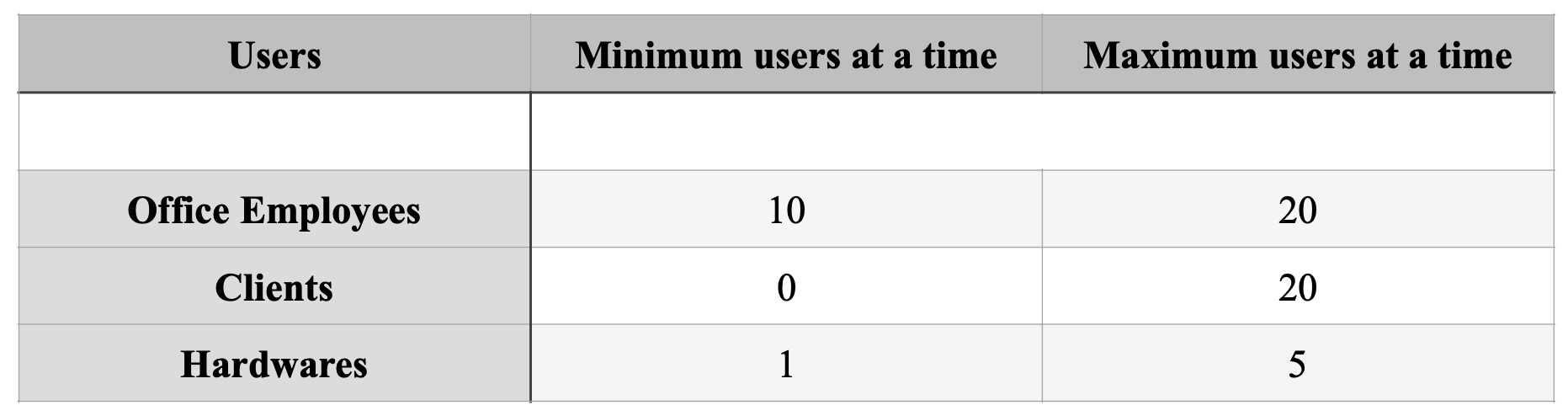
2.4.3 Intended Users
WLAN Network in Utopia Tech is intended for both staff as well as customer usage. To develop a mutual relationship with clients and audiences, employees can use email and social media platforms with network availability. It will also be accustomed to managing reports and the company’s finances through applications like Freshbooks and Wave Accounting. Similarly, clients who visit office premises will also be facilitated with WLAN Network for their amenity.
2.4.4 WLAN Standards and Consideration
Among 1100 or even more operative Wi-Fi standards maintained by IEEE, the 802.11 series standard is studied in detail, as it comprises every LAN (WLANs) and MAN standards(Notes, 2019). There are other handful of standards which include, 802.11a, 802.11b, 802.11g, 802.11n and 802.11p. A comparison between a few of the considerable standards is demonstrated below:
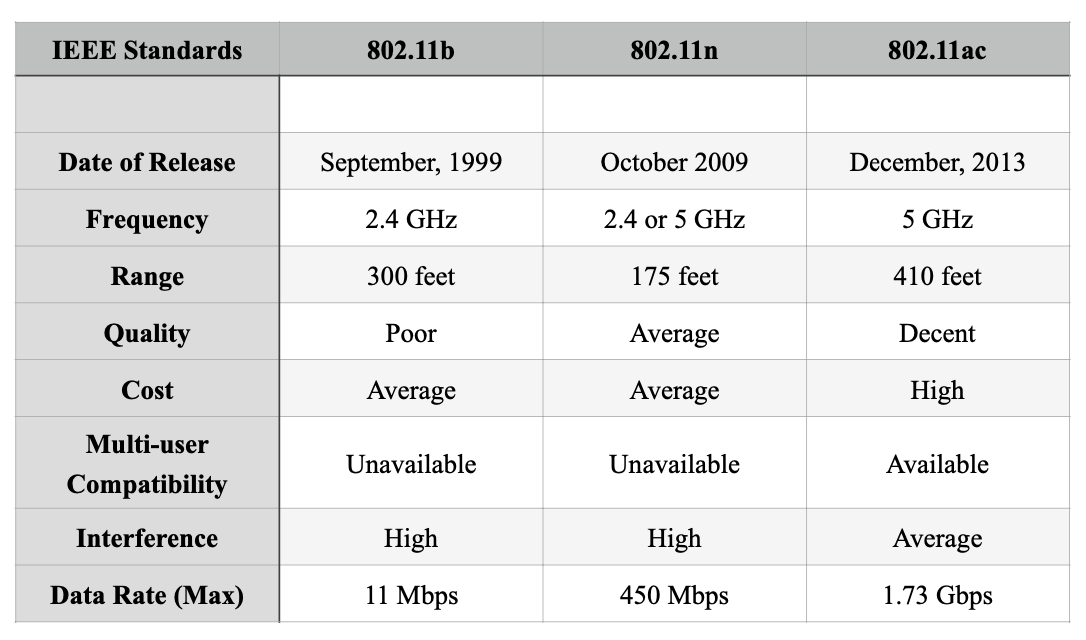
Observing all available wireless standard variations, the recommended one is the IEEE 802.11ac. One of the foremost motives for choosing this particular IEEE standard is because of its broad acceptance proportion among devices like routers and modems. The use of Multi-User MIMO in 802.11ac enhances the network potentiality while its modulation ventures bring 33% inclination in data ratio. Furthermore, 802.11ac provides more than thrice the pace of 802.11n and operates extensive bandwidth which ranges in-between 80MHz - 160MHz (Advantages of 802.11ac | Disadvantages of 802.11ac, 2019).
2.4.4.1 Antennas
Antennas are crucial components of a WLAN system, that uses converted electrical signals to
facilitate wireless signals. The transferring and receiving antennas presented in wireless devices
transform EM packets into electrical signals.
Wi-Fi antennas are categorized into 2 major types: Omnidirectional and Directional. After
studying both of them, the chosen antenna for our site is Ceiling Dome Antennas.
This is because the office will have devices like laptops, PCs, and printers in use and also there
will be other obstacles to create certain interference within the site. An appropriate location is
selected in the ceiling and the antenna is installed with the necessary measurements.˝
2.5 RF and Speed Considerations
During the deployment of a WLAN Network, the range and tempo of radio-frequency are reckoned essential. Several factors play a part in the alteration of radio-frequency. Apart from all those physical obstructions within the site, some other effectual factors are specified below:
2.5.1 Coverage
The WLAN Network coverage is one of the crucial parts to focus on during the deployment process. It determines whether users can get sufficient network on their device to use the high level standard connection. The area (size) of SOHO taken into consideration during the deployment and required access points, signal strength, and data rate are studied to maintain sufficient coverage within the building.
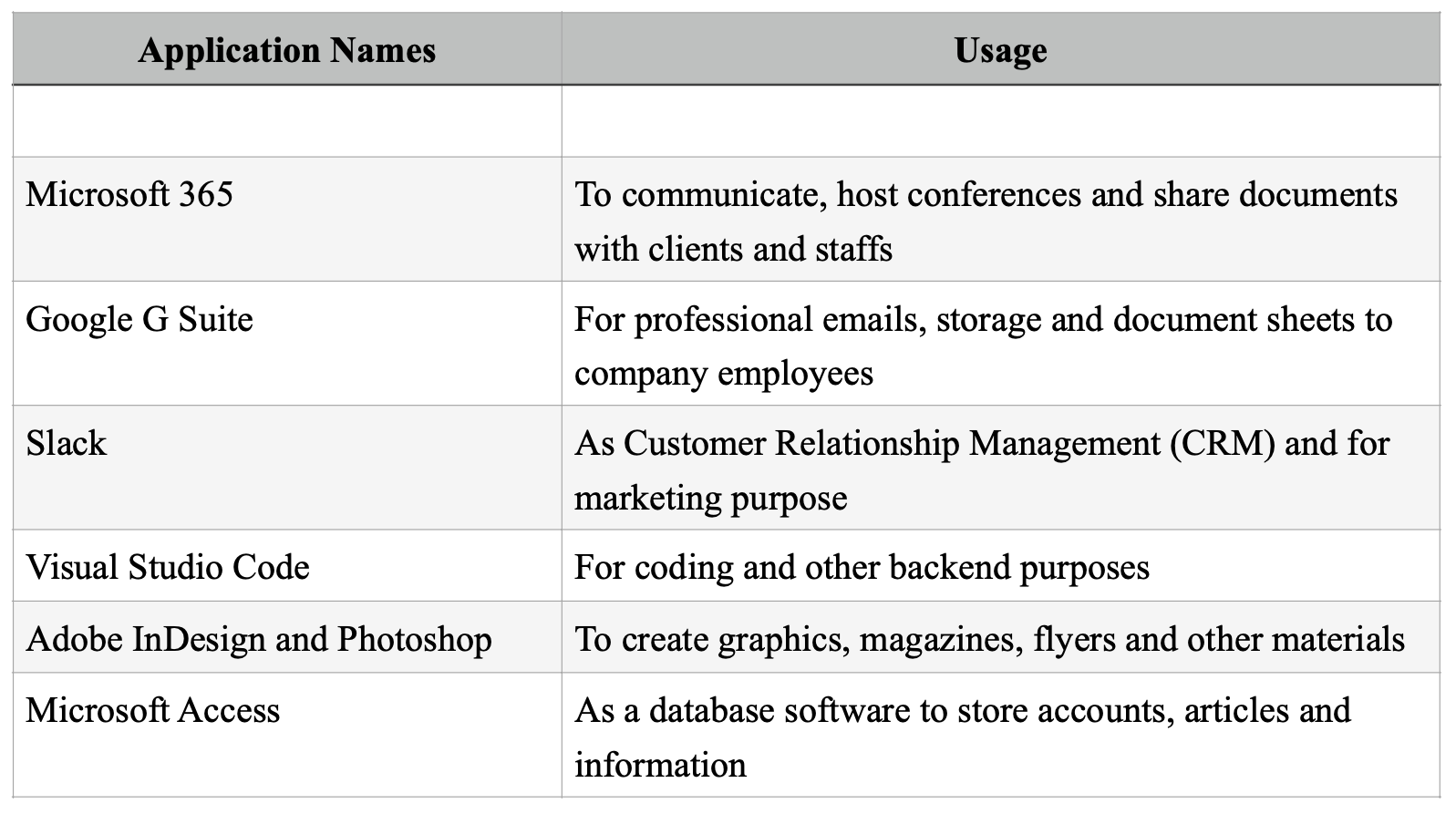
2.5.2 Applications to be used
Utopia Tech, being a startup IT office will use several different applications with the intent of facilitating staff as well as customers. However, some of the major applications that will be used are :
2.5.3 Line of Sight
During WLAN deployment, the propagation of radio signals between transmitter and receiver is considered to be significant. In Line of Sight, the transference occurs when both transmitter and receiver are open without any barriers between them. However, in empirical life, this is pretty much an unrealistic task, not just because of physical obstructions, but also because of natural factors. There are generally two Line of Sight (LoS): Visual and Radio. Visual LoS refers that a transmitter visualizing the receiver while Radio LoS refers to the transmission of radio signals (CAPANO, 2021). During the deployment process, LoS between two stations is studied along with the chosen router and any other selected devices. However since there are a lot of physical obstructions within the site, Radio LoS can be considered as a superior option.
2.5.4 Interference
Radio Frequency Interference (RFI) is the intrusion caused due to excessive radio spectrum occupancy. RFI occurs because of the high amount of transmitters, monitors, or even amplifiers. This causes disarrangements of connections during communication, mislaying of assistance as well as detain in information throughput (Whitlock, 2020).

Figure: Data Flagging Equipment (Innoo Tech, 2021)
Data flagging (RFI detection) is done on the site using an appropriate RFI detecter. For this project, ‘Innoo Tech RFI Detector’ will be used considering its impressive agility and accuracy. By focusing on appropriate routing without needless flooring and with hefty gauge cover wires, interference within the cite area can be controlled.
WLAN Interference
The performance of the selected wireless standard (IEEE 802.11ac) is disrupted by other
networks as WLAN interference. Taking network IEEE 802.15 which encompasses IEEE 802.15.1
(Bluetooth), it distorts the performance of IEEE 802.11ac through the FHSS hops. While
Bluetooth embraces the whole 2.5 GHz band completely, IEEE 802.11ac on the other hand barely
surrounds half of the 2.5 GHz band. This creates a collision among the networks, which ultimately
plunges the performance of IEEE 802.11ac. Other than proximity or Bluetooth devices, there are
other sources of interference such as Microwave oven interference, Radio signals interference,
Cordless phone interference and so on (Cisco Press, 2015).
As a network consultant, appropriate measures are taken during the WLAN planning to avoid
these issues. Devices like microwave ovens and cordless phones will be kept away from Access
Points while wireless cameras should be located at an appropriate distance from WLAN devices to
avoid interference (Huawei Support, 2019).
2.5.5 Environment
The environment is also one of the elements that affect network interference. There are a lot of environmental factors that disrupt the WLAN performance. This involves reflection, diffraction, scattering, refraction, and absorption. These factors hamper the radio frequency, amplitude, bandwidth, and wavelength of a network. To avoid interference because of these environmental problems, the placement of an Access Point in the site is planned in the appropriate position. Furthermore, minimization of the usage of glass or similar products might also aid in reducing the interference in the site.
RF Justifications and Considerations
There are several things to be considered during the RF deployment process. Since the distance between access points can give rise to disparity of throughput, the data standard of access points must be kept in limit. Likewise, the way radiation can be determined is when end users test in repeatedly.
2.6 Site Survey Software
The software used to conduct site surveys for Utopia is Ekahau Site Survey. Operating efficiently for all network ranges, this software is supported both on Windows as well as Mac OS. There are several features such as auto-detection of access points. that made us choose this specific site survey tool. It would help to generate maximum performance from the network.
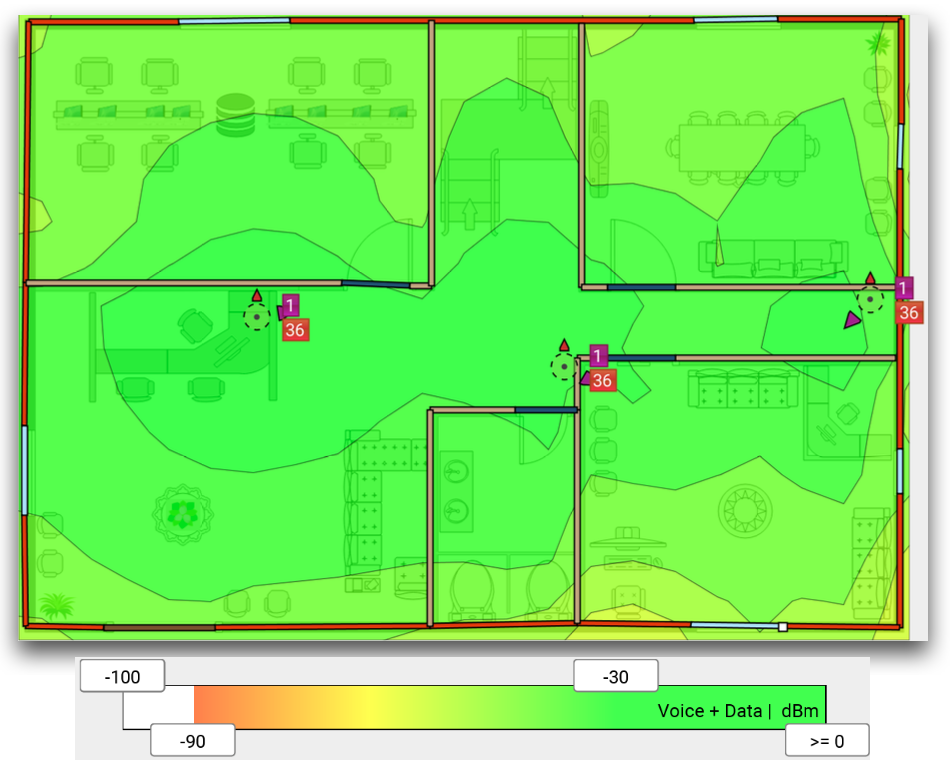
Figure: Heat map view of Site Survey
3. Hardware and Software Requirements
To achieve finest quality of internet facilities in Utopia tech, high quality hardwares and softwares must be deployed, considering the financial limitation of the SOHO tech company. As a network administrator, number of hardwares and software systems are recommended along with relevant justifications.
3.1 Recommended Hardwares
In terms of hardware, we have several networking devices such as routers, access points, ethernet cables, wireless bridge and controller. Necessary comparisons are also done along with their justifications.
3.1.1 Routers
Recommendation and Justification
The recommended router for WLAN deployment in Utopia Tech is Synology RT2600ac. It is a quality-rich router, supporting double WAN connectivity with MU-MIMO data streaming. It is easy to install and distributes unbroken 2.4GHz and 5GHz throughput. The scalable RT2600ac comes with business-grade protection and functions together to cover the surroundings, enlarging the network availability in every corner of the office.

Figure: Synology Router RT2600ac (Synology Inc., n.d.)
Supporting wireless type of 802.11ac, the RT2600ac facilitates with WPS2, WPA-PSK, WPS, WPA2-PSK, and also WEP security protocol. The data transfer rate of this router is 1 GB/sec and the voltage is about 120240 volts. Furthermore, the hardware has a surface coating of 7 traffic authority and it also has a sharp connection for conversion between utmost range and speed. To clarify the effectiveness of the chosen router, a spec comparison is also done with other available options. This allows clients to see the difference between them clearly and have three say during hardware selection.
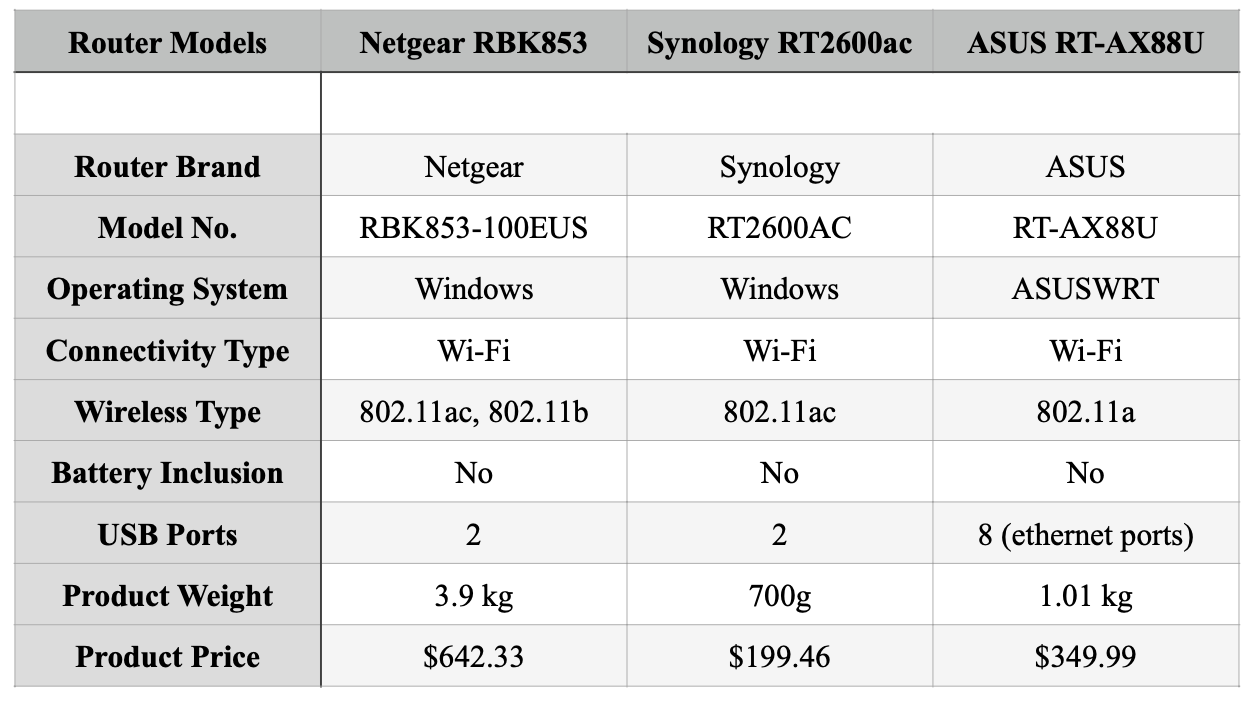
Figure: Comparison of router functionalities
Looking at the comparison table, both Netgear RBK853 and Synology RT2600ac support our recommended IEEE Standard (802.11ac). However, the price of Netgear RBK853 and ASUS RT-AX88U is too much for a small SOHO. Therefore, with the provided justifications and the above comparison, Synology RT2600ac is chosen as it seems to be a feasible option both technically and financially.
3.1.2 Access Points
An access point is used in Utopia to connect routers with the help of ethernet cable so that WLAN connection is available in the projected area. In Utopia Tech, access points are placed in work station area, reception, and meeting room as well. Access points in the station will allow developers to work in an environment having a strong internet connection. Likewise, according to stakeholders, the meeting room usually hosts a high number of people on a regular basis. So, it can be a place that might be advantageous to meeting attendees.
Recommendation and Justification
In terms of Access Points (AP) selection, Ubiquiti UniFi Pro 802.11ac is the recommended one. This 1.75-pound scalable access point is comprised of a UniFi controller, that optimizes RF performance for strong network connections. It is an 802.3af powered AP that is portable for both indoor as well as outdoor operation along with weather resistance support. Likewise, it supports the latest 802.11ac IEEE standard technology along with 3X3 MIMO tech that inclines antennas for transmission and receiving to upgrade WLAN connectivity.

Figure: Ubiquiti UniFi Pro 802.11ac Access Point (telco.sydney, n.d.)
The spectral analyses in Ubiquiti UniFi Pro gather feedback on the entire 5 GHZ while its band steering drives users to quicker interferences. According to expert reviews, this is a hard AP to deploy or set up. However, once the AP is set up by the network administrator, unlimited scalabilities are provided based on its software. It has 2 10/100/1000 ethernet ports and provides 1300 Mbps with 5 GHz speed. Moreover, basic comparisons with other similar access points are given :
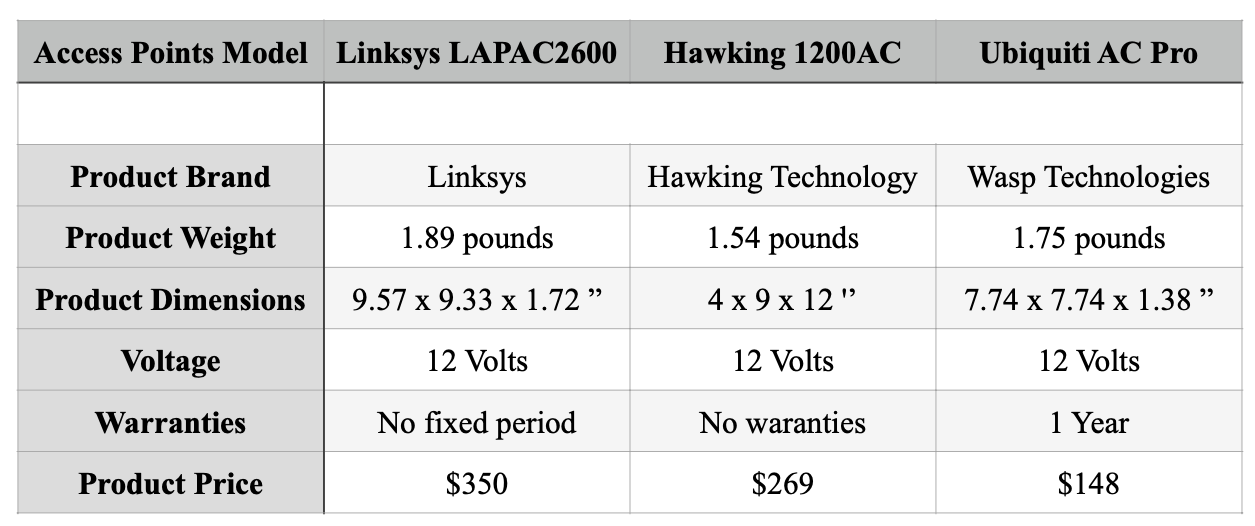
Figure: Comparison of Access Points functionalities
Despite having almost identical functionalities to the other two access points, the Ubiquiti UniFi Pro 802.11ac Access Point is available at a cheaper price compared to others. What’s more , the company is currently providing warranties, that allow stakeholders to choose the device without complications.
3.1.3 Cables
Recommendation and Justification
The use of cables in our deployment process is to connect Access Point to the router. To set up an Access Point, we can simply insert the cable into the LAN port of the router and connect it to the main ethernet post of AP from the other side. This will provide access to shared resources between multiple devices functioning under the same LAN network.

Figure: DiBillion Da Ethernet Cable - Cat 8 (Parrish, 2021)
Since most of the ethernet cables are made up of copper and they use electrical signals for data transmission, the possibility of electromagnetic interference occurs rises significantly. To prevent this, ‘shielded cables’ are used to cushion the wire from any sort of interference or electromagnetic leakages. Ethernet cables are further categorized as ‘Cat’ versions along with their distinctive specifications. Apart from ethernet cables, selection of fiber optic cables is also considered for the side. Basic differences between these cables are demonstrated in the table below:
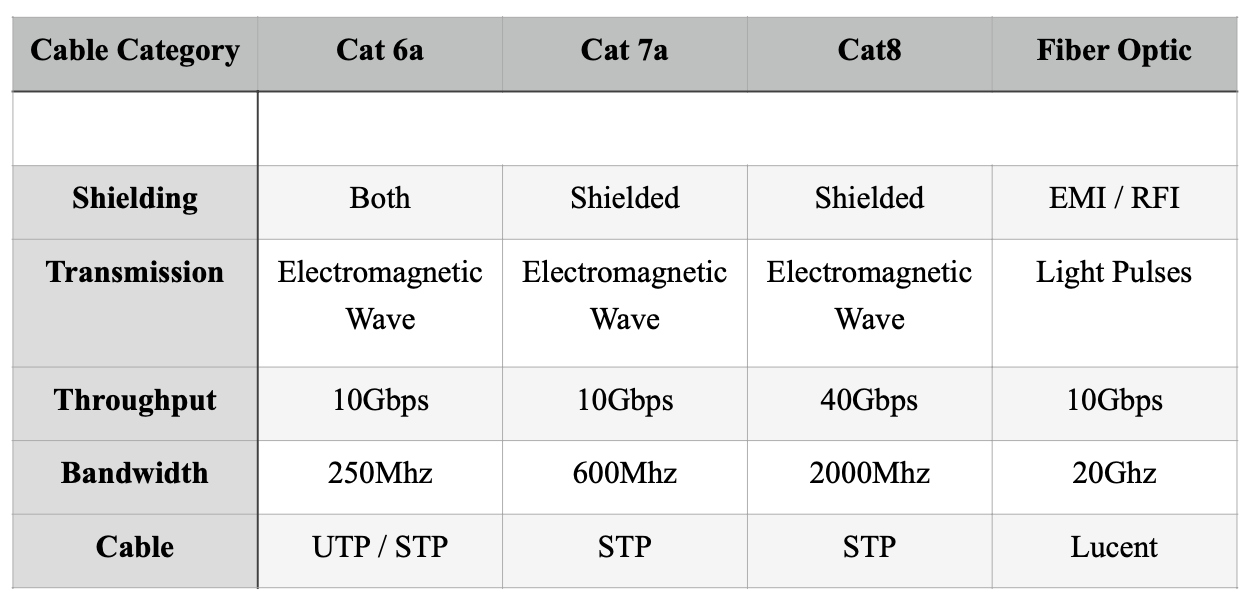
Figure: Comparison of available cables
The above comparisons clarify the differences between ethernet and fiber optic cables. There are a few crucial features in Fiber Optic cables such as light pulse transmission, that make them special. However, considering the fragile nature of Fiber Optic cables, the recommendation is to choose Ethernet cables: either Cat 7a or Cat 8. However, the talk about cables can be done with stakeholders in the meantime and selected wisely without any obfuscation.
3.2 Recommended Software
Security Implementation Requirements
Like hardware, few significant softwares are carefully considered during the WLAN deployment process. With an increasing number of hackers and crackers every day, the system must be prepared to defend against any sort of attack at any time. Firewall installation is considered to be one of the best methods to stay away from network threats and anomalies. However, since this deployment is for an SOHO environment, usage of a firewall does not make sense: financially and based on the number of users. This is why, Intrusion Detection Software (IDS) and Antivirus are recommended to maintain system security in Utopia Tech.
3.2.1 Intrusion Detection Software
An Intrusion Detection System (IDS) is a security software that diminishes security threats such as cyber-attacks and malware. Furthermore, IDS also blocks upcoming threats that might harm the system by accessing it in an unauthorized way. The main reason to install an Intrusion Detection System in a system is because it alerts system administrator in case of any suspicious activities, by monitoring network traffic of the environment. The IDS is further classified into two major types: Host Intrusion Detection Software (HIDS) and Network Intrusion Detection System (NIDS).
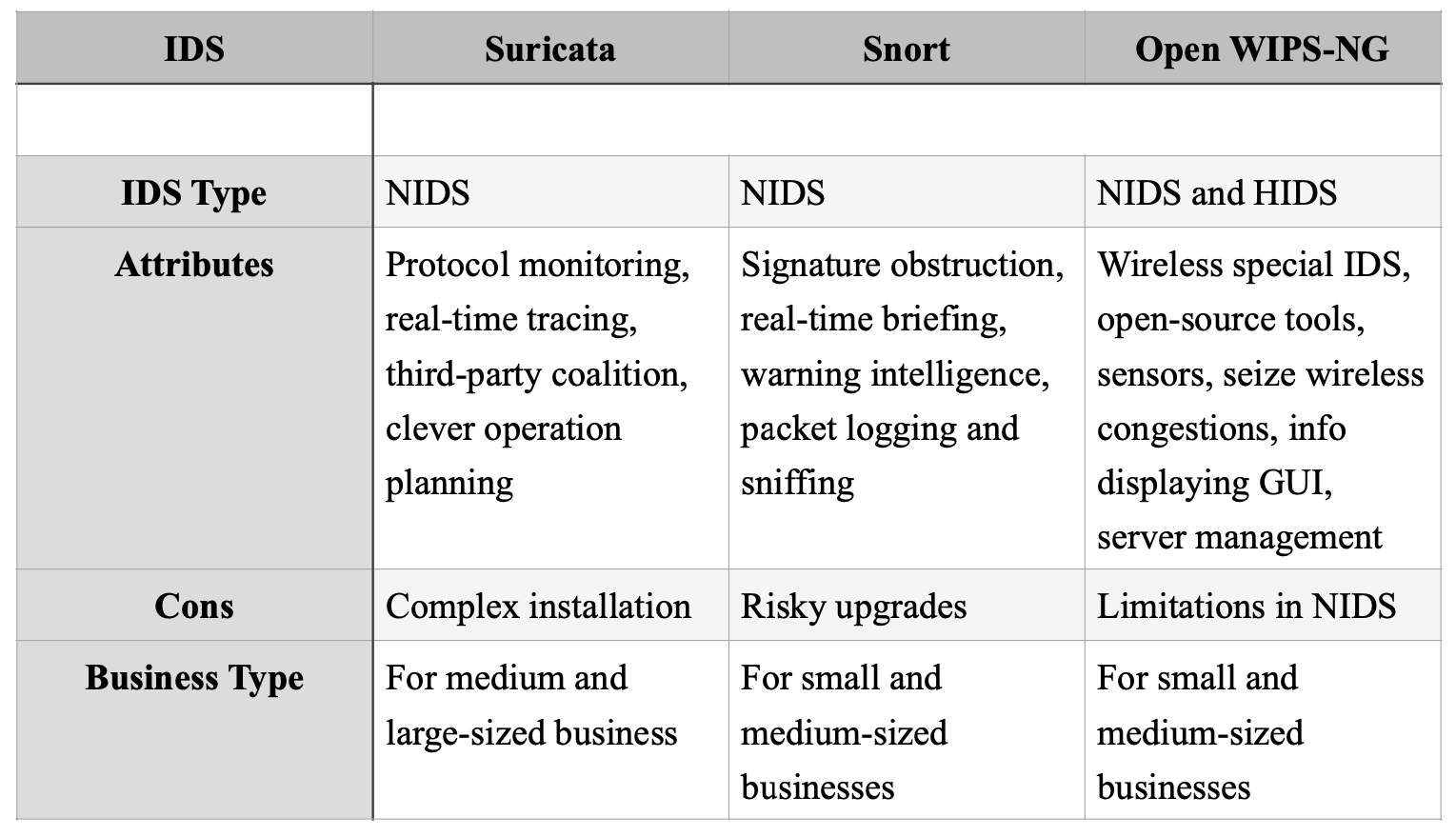
Figure: Comparison of available IDS
After analyzing all available Intrusion Detection Software, the chosen IDS for Utopia Tech is the ‘Open WIPS-NG’ IDS. This is because the software is specifically built for wireless system protection and the available features match our expectations. However, Snort IDS seems to have problems with scalability and Suricata is used in large-scale businesses rather than SOHO companies like Utopia Tech.
3.2.2 Antivirus
Along with devices like laptops and smartphones, routers are also among the top targets for hackers lately. These network users can easily break the vulnerability of routers to find sensitive data such as bank credentials and private information. These credentials might further be used to steal or for other illegal works. To assure security to all WLAN users in Utopia Tech, the installation of Antivirus is considered crucial. Some of the available Antivirus and their functionality comparisons are shown in the table:
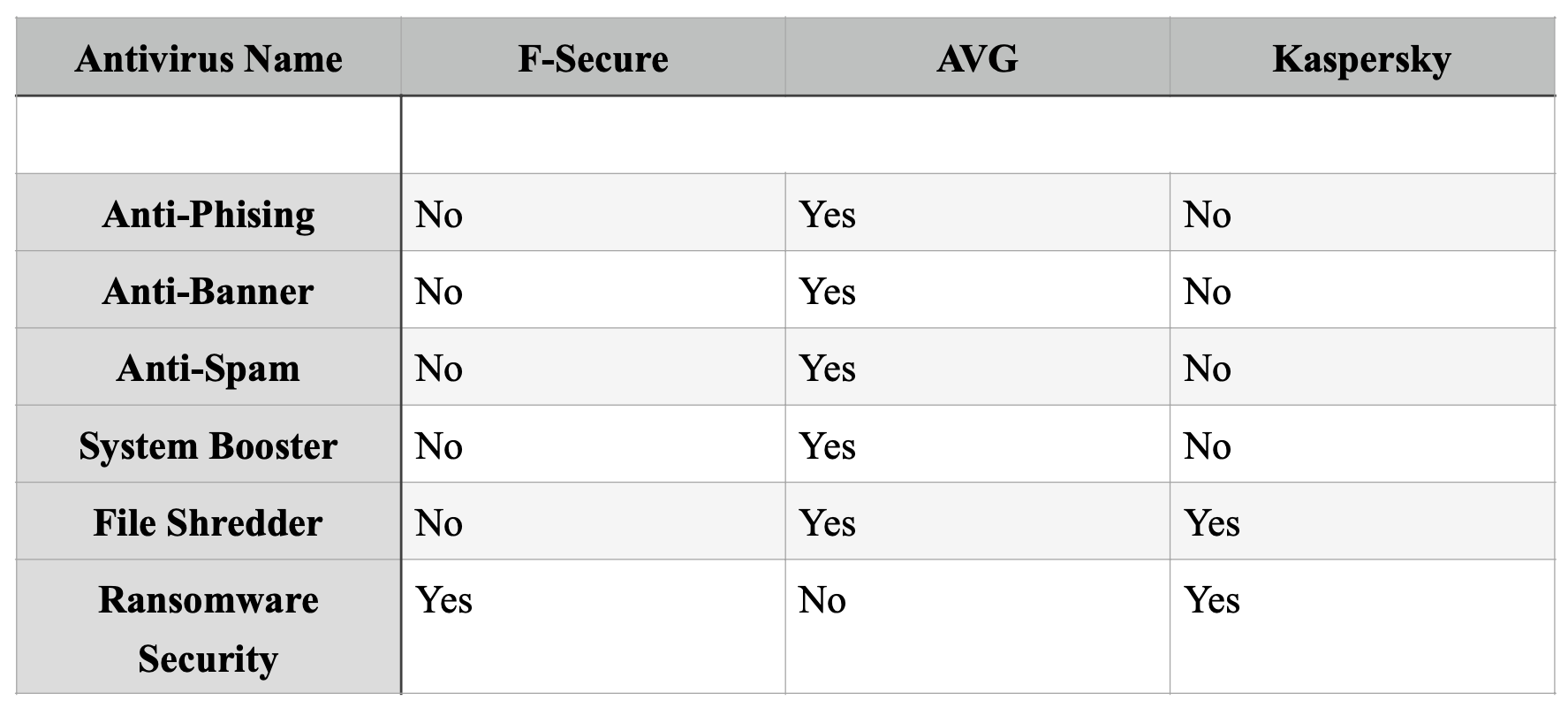
Figure: Comparison of Antivirus functionalities
Considering the comparisons above, the AVG (Antivirus Guard) is an obvious choice as our antivirus software. The features of AVG that include total internet security from phishing or spam are something we were looking for. The antivirus software further scans emails and mends virus-infected files to keep the system secured. The online shield in AVG also guarantees the safety of data exchanges through instant messengers (Wikipedia contributors, 2021a). This way, the WLAN system can be brought into use, without any fear of being attacked or tricked.
4. Conclusion
The deployment process assured detailed information about all the crucial factors, methods, and procedures of Wireless Local Area Network setup. The site survey conducted during the WLAN deployment produced several learning opportunities and few complications to solve. Likewise, the project also created a chance to learn about network hardware and software in depth. In a nutshell, wireless LAN is deployed in an SOHO environment and the internet can be accessed as well. External RF interferences were detected and necessary actions were taken to troubleshoot them and facilitate the best possible internet coverage.
References
Advantages of 802.11ac | disadvantages of 802.11ac. (2019, January 15). RF Wireless
World. https://www.rfwireless-world.com/Terminology/Advantages-and-
Disadvantages-of-802-11ac.html
CAPANO, D. A. N. (2021, April 25). Control Engineering | Wireless line-of-sight, non-
line-of-sight, beyond-line-of-sight propagation. Control Engineering. https://
www.controleng.com/articles/wireless-line-of-sight-non-line-of-sight-beyond-
line-of-sight-propagation/
Cisco Press. (2015, June 15). Radio Signal Interference > Wireless LAN Implications,
Problems, and Solutions. Cisco- Networking, Cloud and Cybersecurity
Solutions. https://www.ciscopress.com/articles/article.asp?
p=2351131&seqNum=2
Huawei Support. (2019, June 12). Where Are Interference Sources in WLAN and How Is
the Interference Strength? - AR500, AR510, and AR530 V200R007 CLI-based
Configuration Guide - WLAN-FAT AP - Huawei. Huawei. https://
support.huawei.com/enterprise/en/doc/EDOC1000151733/8215e3a1/where-are-
interference-sources-in-wlan-and-how-is-the-interference-strength
Innoo Tech. (2019). Amazon.com: Innoo Tech Anti Spy Detector & Camera Finder RF
Signal Detector GPS Bug Detector Hidden Camera Detector for GSM Tracking
Device GPS Radar Radio Frequency Detector: Electronics. Amazon. https://
www.amazon.com/Innoo-Tech-Detector-Tracking-Frequency/dp/B07XDT9TGG/
ref=sr_1_2?
dchild=1&keywords=radio+frequency+detector&qid=1626629972&sr=8-2
Notes, E. (2019, July 18). WiFi Standards: IEEE 802.11 » Electronics Notes. Electronics
Notes. https://www.electronics-notes.com/articles/connectivity/wifi-
ieee-802-11/standards.php
Parrish, K. (2021, February 5). The best Ethernet cables for 2021. Digital Trends. https://
www.digitaltrends.com/computing/best-ethernet-cables/
Porter, D. (1997). Internet Culture (1st ed., Vol. 1). Routledge. https://doi.org/
10.4324/9780203699560
Sauter, K. (2008, April 29). Active vs. predictive site surveys: pros and cons. Network
World. https://www.networkworld.com/article/2278470/active-vs--predictive-
site-surveys--pros-and-cons.html
Site Survey Tool - TamoGraph - Understanding Survey Types: Passive, Active, and
Predictive. (n.d.). TamoSoft. Retrieved June 7, 2021, from https://
www.tamos.com/htmlhelp/tg/understanding_survey_types_pas.htm
Synology Inc. (n.d.). Synology RT2600ac │ AC2600 high-speed Wi-Fi router │ Parental
controls & security │ | Synology Incorporated. Synology. Retrieved August 13,
2021, from https://www.synology.com/en-global/products/RT2600ac
telco.sydney. (n.d.). Ubiquiti Unifi UAP-AC-PRO. Retrieved August 16, 2021, from
https://telco.sydney/products/ubiquiti-unifi-uap-ac-pro
Top 10 BEST Intrusion Detection Systems (IDS) [2021 Rankings]. (2021, August 6).
Software Testing Help. https://www.softwaretestinghelp.com/intrusion-
detection-systems/#4_Snort
Whitlock, B. (2020, July 6). UNDERSTANDING and controlling RF interference. Sound
& Video Contractor. https://www.svconline.com/resources/understanding-and-
controlling-rf-interference-364849
ZVANOVEC, S., PECHAC, P., & KLEPAL, M. (2003). RADIOENGINEERING (4th ed.,
Vol. 3). Radioeng.
